Introduction: The Growing Importance of AI in Modern Cybersecurity
Cyber threats today don’t just move faster and hit harder; they shape-shift and also morph in ways that leave old-school, manual defenses scrambling to keep up. Organizations are scattered across cloud networks (internet-based computing services that store and process data online). They also consist of or connect mobile devices (portable computing devices like smartphones and tablets), IoT gadgets (Internet of Things, physical devices that connect to the internet to collect and exchange data, such as smart thermostats or security cameras), and sprawling supply chains (complex networks of partners and vendors involved in producing and delivering goods and services). The attack surface keeps growing, and the old playbook just can’t keep up.
Attackers thrive in this chaos. They use automation (technology that performs tasks without human intervention, such as running attacks or scanning systems automatically) and anonymity (methods to avoid revealing identity online, like using fake credentials or encrypted networks) as their secret weapons to strike at scale and slip away unseen. Artificial Intelligence steps into the fray, a tool that can just as easily tilt the odds for defenders as for those on the attack.
AI’s relevance in cybersecurity lies beyond processing data quickly. It detects patterns, adapts on the fly, and enables real-time responses. As attackers become more sophisticated, defenders must adapt. For anyone new to the field, grasping how AI is reshaping cyber defense isn’t optional; it’s the foundation for both practice and research.
We’ll start with the basics, dig into the risks and defensive power of AI, tackle the ethical puzzles, and finish with a glimpse at what’s next.
Foundational Concepts: AI and Machine Learning in Cyber Defense
In cybersecurity, AI mostly shows up in the form of machine learning (ML). ML is all about systems that learn from data instead of following set rules. Old-school security tools rely on fixed patterns to catch threats, but they’re blind to anything new or unexpected.
Machine learning flips the script. These models chew through mountains of data, structured (organized, labeled data such as logs or records) or messy (unstructured data like emails or open text), to spot oddities (anomalies), sort behaviors, and even guess what an attacker might do next. In cybersecurity, you’ll see supervised learning (models trained with labeled data, e.g., known malware samples) for things like malware detection. Unsupervised learning (models that find patterns in unlabeled data) is used for catching weird network activity. Reinforcement learning (systems that learn through feedback and trial-and-error to improve decisions) is used for systems that adapt their defenses on the fly.
You’ll find these models everywhere, on endpoints, across networks, inside apps, and tracking user behavior. The payoff? Security teams stop playing catch-up and start getting ahead. But it only works if the data is solid, the context is sharp, and reality checks are routine. That’s what keeps the models honest.
The Adverse Use of AI in Cybersecurity
AI isn’t just in the hands of defenders. Attackers are using it too, automating their recon, sharpening their attacks, and sneaking past defenses. Picture phishing emails that feel personal and hit your inbox at exactly the wrong time. Algorithms, not people, are behind them. This new breed of attack leaves the old spray-and-pray tactics in the dust.
Adversarial machine learning takes it further. Attackers poison training data, slip in misleading inputs, or dissect algorithms to find weak spots. Sometimes, a tiny change fools a model into missing a real threat. For anyone relying on AI to keep things safe, that’s a serious headache.
Bottom line: AI does not eliminate cyber risk; rather, it changes the nature of these risks. Building resilient systems requires understanding both how AI enhances security and how it can be exploited.
AI as a Defensive Force Multiplier in Cybersecurity
AI works best as backup for human analysts. With the right support, security teams can spot what matters and move faster when trouble hits.
Threat Detection and Anomaly Analysis
AI-driven tools are quick to notice when something’s off, whether it’s a strange network spike, a rogue endpoint, or a user acting differently than usual (out-of-character behavior).
Unlike signature-based security systems (which rely on lists of known threats, known as “signatures,” to identify attacks), these models can spot attacks no one’s seen before. This is crucial for detecting zero-days (previously unknown vulnerabilities that have not been patched or identified by software makers) and stealthy threats. Research indicates that, in busy environments, machine learning often outpaces the old methods, especially when things get hectic.
Security Operations and Incident Response
In Security Operations Centers (SOCs), teams are responsible for monitoring and addressing security incidents. AI helps sort alerts, links related incidents (correlation, or linking different incidents to spot coordinated attacks), and adds context that would take humans hours to piece together. Automating repetitive tasks frees up analysts to zero in on complex problems.
Natural language processing (NLP, a technology for understanding and analyzing human language, like reading security reports) enables teams to sift through mountains of threat reports and hacker chatter efficiently. This data-driven prioritization (sorting alerts by likelihood or severity of risk using data models) aligns defensive resources with actual threat likelihood.
This approach is increasingly emphasized in frameworks from organizations such as NIST (National Institute of Standards and Technology) and ENISA (European Union Agency for Cybersecurity).
Behavioral Biometrics and Identity Security
Machine learning is also shaking up identity security(proving that a user is who they claim to be, using credentials or unique patterns), too. By tracking indicators, known as behavioral biometrics (using unique behavior patterns to verify identity, such as keystroke rhythm or mouse movement), it can provide ongoing verification that you are the legitimate user. The result? Defenses grow stronger against stolen logins, but users don’t have to jump through extra hoops.
Ethical, Operational, and Governance Challenges
Rolling out AI in cybersecurity isn’t just about tech; it’s about ethics, too. How do these models make decisions? Can we explain them? Who takes the blame when things go sideways? These questions matter most when privacy or access is at stake.
Bias in training data can lead to disproportionate false positives (incorrectly blocking legitimate actions or users) or false negatives (failing to detect actual threats), potentially affecting specific use cases. If the data feeding these models is biased (skewed or unrepresentative), the fallout can be real. Some users get flagged for no reason. Others sneak past. This is where cybersecurity, ethics, and policy need to work together, not in isolation.
Lean too hard on automation, and you risk missing what matters. That’s why frameworks stress keeping humans in the loop. AI should back up expert judgment, not replace it. For students, these challenges are a chance to dig into responsible AI development and real-world testing.
Future Trends and Research Opportunities
Looking forward, AI in cybersecurity is spreading out and drilling down. Researchers are trying federated learning to catch threats without sacrificing privacy. Graph-based models are mapping out complex attack paths. Some teams are even building systems that patch themselves as they go.
Another big move: mixing AI with threat intelligence to predict attackers’ next steps. But the arms race is far from over. Defending against attacks that target the AI itself is still an open challenge. The stakes? National security and critical infrastructure are on the line.
For students and researchers, the field is shifting fast. Success now means knowing data science, system security, and ethics. Real progress comes from connecting theory to hands-on testing and what actually works in the wild.
With all these changes, one thing’s clear: being ready for AI-driven shifts is now a must for anyone in cybersecurity.
AI is changing the game in cybersecurity. It’s not a magic fix, but it’s essential for building smarter, more flexible defenses. The real challenge is seeing both the risks and the rewards, and getting ready to use AI wisely.
For newcomers, jumping into AI and cybersecurity isn’t just about learning new tricks. It’s a chance to see how technology, risk, and trust connect in the digital world. Ask tough questions. Test boundaries. Push research forward and help build systems people can actually trust.
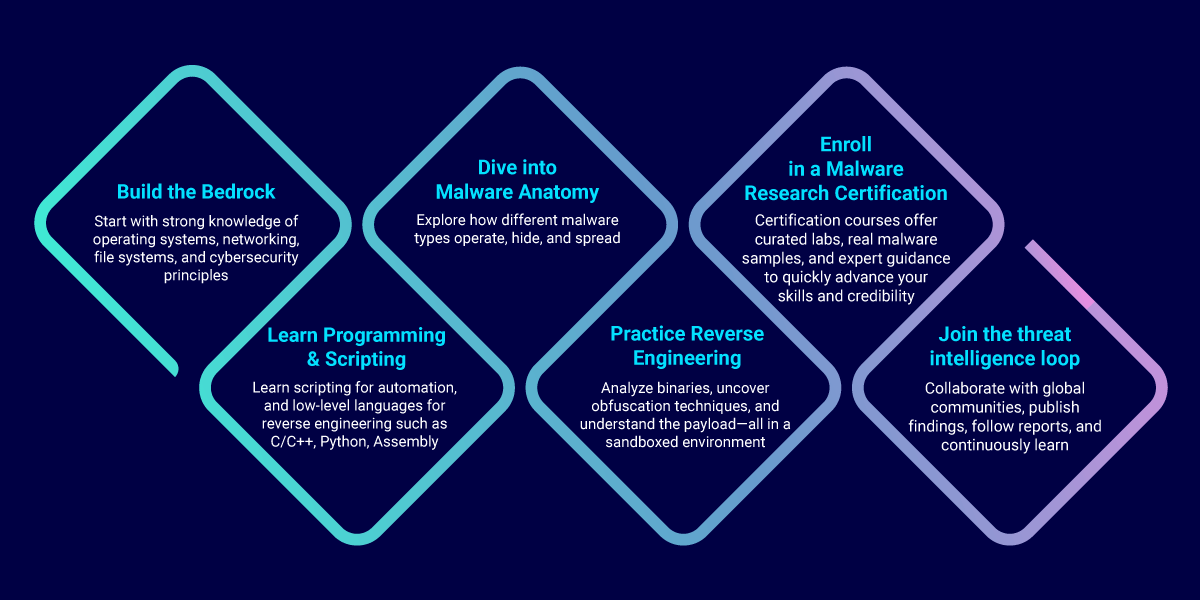
Skills Cybersecurity Students Should Develop
To work effectively with AI-driven security tools, students should focus on a blend of data literacy and traditional defensive tradecraft. You do not need to build AI models from scratch, but you must understand how they work, why they fail, and how attackers try to bypass them.
1. Basics of Machine Learning and Data Analysis
The goal here isn’t to become a data scientist, but to understand the math under the hood. You should be comfortable with how a model moves from raw data to a decision.
- Feature Engineering: Learn how security data (like a packet header or a file size) is turned into a numerical feature that a model can understand.
- Model Evaluation: Understand the difference between a False Positive (a benign file flagged as malicious) and a False Negative (a malicious file that slips through). In a professional SOC, a model with a $99\%$ accuracy rate might still be a failure if it generates 10,000 false alerts a day.
- Data Quality: Learn to spot garbage-in, garbage-out scenarios. If a model is trained on outdated traffic patterns from 2015, it won’t catch a modern ransomware strain.
2. Understanding AI Integration in Security Toolsets
Modern enterprise environments rely on a stack of tools that now come pre-loaded with AI modules. You need to know where the automation ends and your job begins.
- EDR (Endpoint Detection and Response): These tools live on laptops and servers. You should understand how they use behavioral heuristics to stop a process that suddenly starts encrypting files, even if that process isn’t a known virus.
- SIEM (Security Information and Event Management): The SIEM is the brain of the SOC. Learn how it uses AI to cluster thousands of isolated events into a single, coherent incident.
- UEBA (User and Entity Behavior Analytics): This is about spotting the insider threat. If an accountant suddenly starts accessing engineering servers at 3:00 AM, UEBA flags it as an anomaly based on that user’s specific historical baseline.
3. Log Analysis and Behavioral Detection
AI is great at spotting outliers, but it’s terrible at understanding why they happened. Your job is to provide that context.
- Telemetry Literacy: You should be able to read raw logs from Windows Event Viewer, Sysmon, or cloud providers like AWS CloudTrail.
- Pattern Recognition: While the AI might flag unusual PowerShell execution, you need to determine if that script was a legitimate admin task or a Living off the Land (LotL) attack, where a hacker uses your own tools against you.
4. Threat Modeling and Attacker Tactics (MITRE ATT&CK)
To defend a system, you have to think like the person trying to break it. The MITRE ATT&CK framework is the industry-standard periodic table of hacker techniques.
- Mapping AI to Tactics: Learn which stages of an attack, like Initial Access or Lateral Movement, are most easily spotted by AI, and which ones (like social engineering) still require a human eye.
- Adversarial Mindset: Study evasion techniques, such as adversarial perturbations, where an attacker makes tiny, invisible changes to a malware file to trick a scanner into thinking it’s a harmless PDF.
5. Scripting for Automation and Data Handling
Automation is the bridge between a mountain of data and a fast response.
- Python: The undisputed king of both AI and security. Use it to parse JSON logs, interact with security APIs, or write scripts that automatically isolate an infected host the moment an AI alert triggers. Here are the Python libraries every cybersecurity student should know:
- Data Processing and AI: Pandas, NumPy, Scikit-Learn, etc.
- Network Security & Analysis: Scapy, PyShark, Impacket, etc.
- Malware Analysis & Forensics: YARA-Python, Volatility, PEfile, etc.
- Automation & Infrastructure: Requests, Paramiko/Netmiko, Cryptography, etc.
You don’t need to master every tool in the box. Nail down a few, like Requests, Pandas, and Scapy, and you’ll be able to pull data from APIs, clean it up, and see how it travels across the network.
- Regex (Regular Expressions): This is a vital skill for filtering through massive datasets. A single well-crafted regex string can find a hidden IP address in a sea of ten million log entries.
Career Impact for Students
AI is reshaping cybersecurity roles, not eliminating them. The entry-level job is evolving away from mindless clicking and toward high-level investigation.
The Shift in the SOC
In the past, a Tier 1 Analyst might spend eight hours a day looking at Level 1 alerts, mostly low-level noise. Today, AI handles that noise.
- The New Entry-Level: Entry-level analysts now work alongside automated systems. Their value comes from interpreting AI-generated insights, investigating complex incidents that the model found suspicious but inconclusive, and improving detection logic so the system doesn’t make the same mistake twice.
- Human-in-the-Loop: You act as the sanity check. When an AI recommends blocking a critical business server because of unusual traffic, you are the one who decides if that block will save the company or shut down the payroll department.
Competitive Advantage
Students who understand both cybersecurity fundamentals, the boring stuff like TCP/IP networking and operating system internals, and AI concepts will have a massive advantage.
- Blue Teaming: You’ll be better at tuning defenses to reduce alert fatigue.
- Threat Hunting: Instead of waiting for an alarm to go off, you’ll use AI-driven datasets to proactively search for quiet attackers who are hiding in the noise.
- Incident Response: You’ll be able to use AI to reconstruct an attack timeline in seconds, rather than days.
The future of the field belongs to the Hybrid Defender, someone who treats AI as a powerful, yet fallible, teammate. By mastering these skills now, you aren’t just learning a tool; you’re future-proofing your career against the next decade of digital warfare.